- 6 Minutes to read
- Print
- DarkLight
- PDF
Auditing SMB File Access
- 6 Minutes to read
- Print
- DarkLight
- PDF
The CTERA Edge Filer provides audit logs of the SMB file access operations performed on the CTERA Edge Filer. This enables organizations to ensure compliance with internal policies and regulations.
The SMB audit log does not record sync operations between the CTERA Edge Filer and a CTERA Portal.
To enable SMB audit logs:
In the Configuration view, select Log Viewer > Audit Logs in the navigation pane.
The Audit Logs window is displayed.
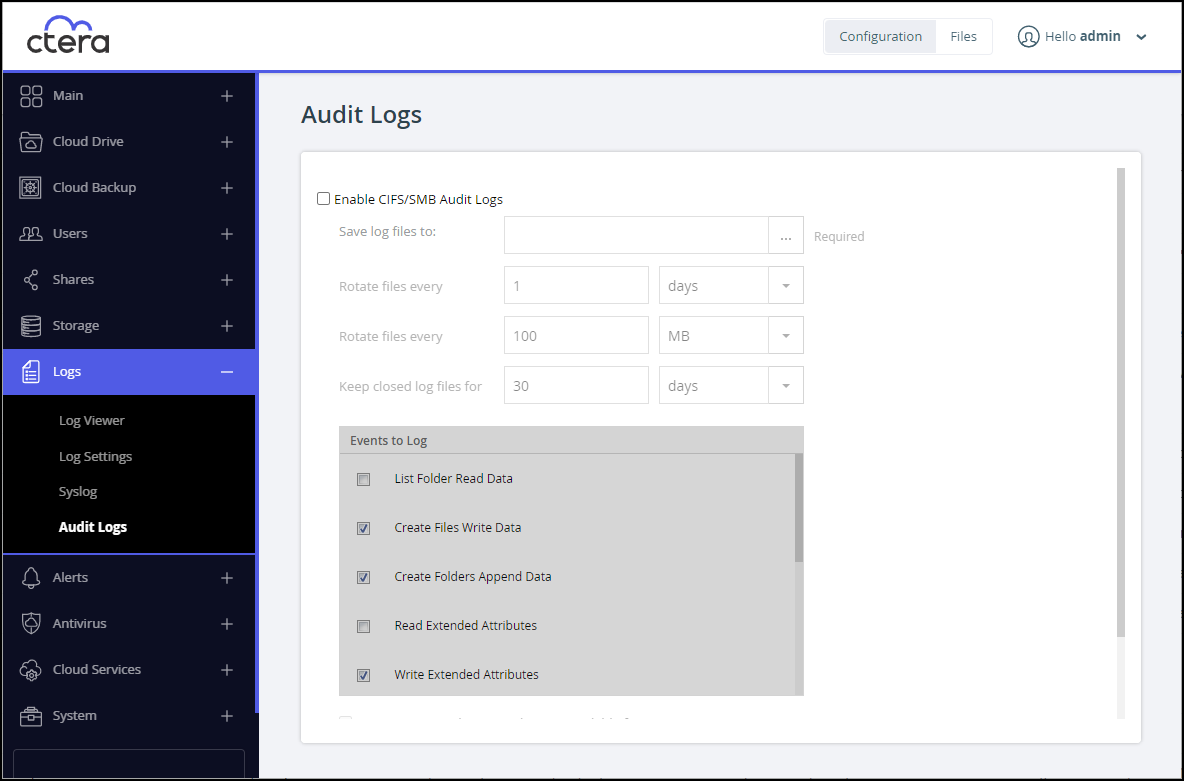
Select the Enable CIFS/SMB Audit Logs option.
In the Save log files to field, click
....If you have created network shares, the following window is displayed, listing the network shares.
Select the network share for the destination to save the log files.
Click Close if you want to create a different network share for the audit logs and then create the network share, as described in Managing Network Shares.If you have not created a network share, the following window is displayed.
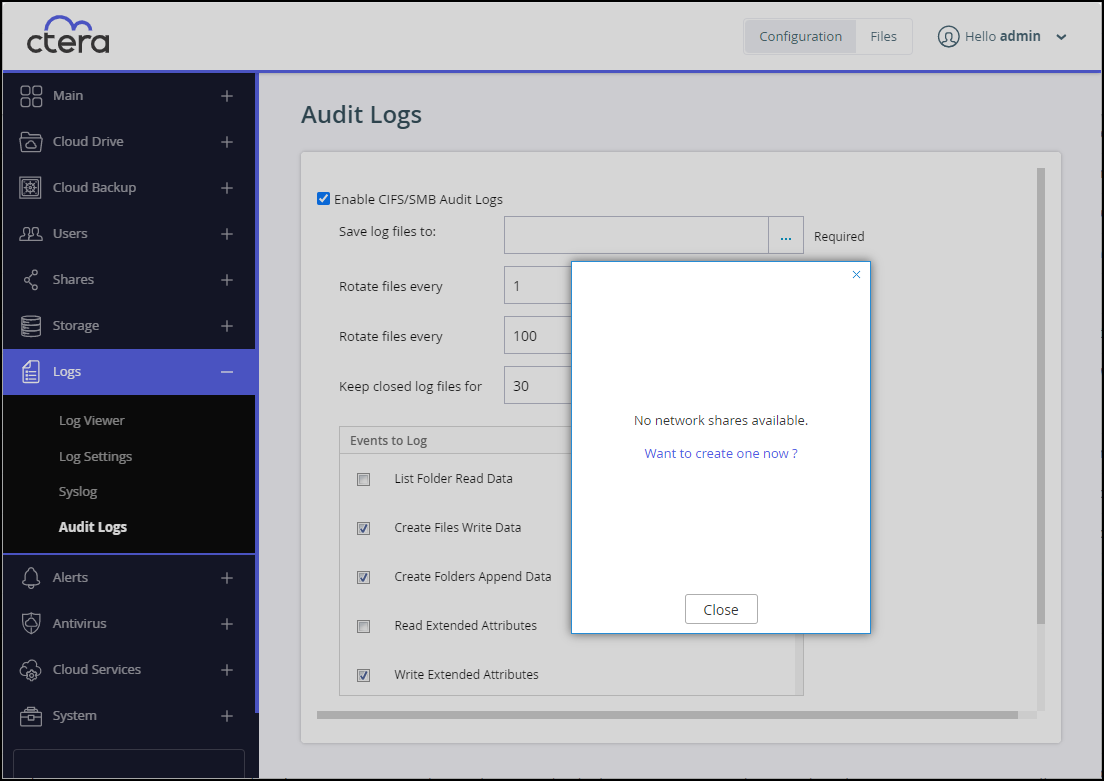
- To create a network share to use as the destination for the audit logs, click the Want to create one now? link.
The Select a Folder to Share wizard opens, displaying the volumes and folders on the CTERA Edge Filer. - Follow the wizard to define the network share, as described in Managing Network Shares.
The network share is selected as the destination to save the log files.
Click Close if you do not want to create a network share for the audit logs.
- To create a network share to use as the destination for the audit logs, click the Want to create one now? link.
The audit log will be saved to /network_share/audit.log.dir/audit.log.
Optionally change the following logging details as desired:
Rotate files every – How often to rollover the log files. You can define the rotation time in minutes, hours or days.
Rotate files every – When to rollover the log files if they grow large. You can define the rotate size in KB, MB, or GB.
Keep closed files for – The number of days to keep closed log files.
A background task is run every 10 minutes and checks these values. For example, if the time to rotate the file has passed or if the size is over the specified size the log file is rotated. Note that this can mean that the file can be larger than the specified value as it will grow until the 10 minute check is performed.
The task also checks if closed log files have exceeded the specified time and any closed log file that has exceeded this time is deleted.In the Events to log area, optionally change the events to log, based on your organization's needs. To add or delete events to log, scroll through the list and select or clear the appropriate check boxes. The events you can log are:
Flag in User Interface Meaning List Folder Read Data Log when data is read from a file. Create Files Write Data Log when data is written or appended to a file. Create Folders Append Data Log when a directory is created. Read Extended Attributes Log when an extended attribute is fetched. Write Extended Attributes Log when an extended attribute is replaced or a new extended attribute is created. Traverse Folder Execute File Log an attempt to open a file. Delete Subfolders and Files — Write Attributes Log when the file attributes, such as the system and hidden attributes, are changed. Delete Log when a file or directory is deleted. Change Permissions Log any change to a file or directory access permission. Change Owner Log when the owner of a file or directory is modified. Check Log permission changes in human readable format, for changes in ACL permissions to files and folders to be reported in the audit log in an understandable format. Where:
ace-type indicates the type of ACE (allow/deny)
ace-rights indicates the type of permissions/AccessMask
ace-flags indicates the ACE behaviorNoteSetting the log to be readable degrades performance.
Click Save.
CTERA Edge Filer generates audit log messages upon various operations.
Example Log Entries
open
Dec 30 08:33:42 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=open|timestamp=1609310022|local_time=1609302822|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/CopiedFile - Copy.png|access=01101001100000000100100000000000|remote hostname=10.212.134.55||
OpenDenied
Dec 30 08:34:06 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|fail|0xc0000034|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=OpenDenied|timestamp=1609310046|local_time=1609302846|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/E0EAEC4D.tmp|access=00000100000000000000000000000000|remote hostname=10.212.134.55|isDir=1||
read
Dec 30 08:33:41 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=read|timestamp=1609310021|local_time=1609302821|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/CopiedFile - Copy.png|type=file|remote hostname=10.212.134.55|fileSize=148071|dataRW=4096||
write
Dec 30 08:33:51 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=write|timestamp=1609310031|local_time=1609302831|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/~$w Microsoft Word Document1.docx|type=file|remote hostname=10.212.134.55|fileSize=54|dataRW=113||
move
Dec 30 08:34:06 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=move|timestamp=1609310046|local_time=1609302846|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|source path=users/portal admin/My Files/Photos/New Microsoft Word Document1.docx|destination path=users/portal admin/My Files/Photos/E0EAEC4D.tmp|type=file|remote hostname=10.212.134.55||
create
Dec 30 08:33:51 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=create|timestamp=1609310031|local_time=1609302831|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/~$w Microsoft Word Document1.docx|type=file|remote hostname=10.212.134.55||
delete
fail operation
Dec 30 08:33:42 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|fail|0xc0000034|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=delete|timestamp=1609310022|local_time=1609302822|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/._CopiedFile - Copy.png|type=file|remote hostname=10.212.134.55|fileSize=18446744073709551615|dataRW=18446744073709551615||
ok operation
Dec 30 08:33:42 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=delete|timestamp=1609310022|local_time=1609302822|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/CopiedFile - Copy.png|type=file|remote hostname=10.212.134.55|fileSize=18446744073709551615|dataRW=18446744073709551615||
setattrib
Dec 30 08:33:42 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|ok|0x00000000|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=setattrib|timestamp=1609310022|local_time=1609302822|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=users/portal admin/My Files/Photos/CopiedFile - Copy.png|dosattrib=0000|remote hostname=10.212.134.55||
getea
Dec 29 10:30:47 2020EdgeFiler smbd: |2020EdgeFiler|ctera_audit|fs|fail|0xc0000225|user=2020EDGEFILER\admin|sid=S-1-5-21-2761415951-3033486807-2004858877-1402|op=getea|timestamp=1609230647|local_time=1609223447|rootPath=/var/vol/syncgateway/cloudshare|share=cloud|path=/var/vol/syncgateway/cloudshare|att=org.netatalk.Metadata|remote hostname=10.212.134.70||
Each field in the message is separated by the | character. The fields in the examples have the following meaning:
Timestamp and edge filer name – Each line in the audit log starts with the timestamp when it was written to the log and the edge filer connected to. For example, Dec 30 08:33:42 2020EdgeFiler smbd:
Edge filer name – The name of the device on which the operation was executed. For example, 2020EdgeFiler.
Log name – The name of the audit log: ctera_audit.
Type – The audit type.
Operation result – The result, either ok or fail.
Operation result code – The result code for the operation. 0xc0000000 for ok. fail is 0xc0000225.
User name – The name of the user who executed the operation. For example, user=2020EDGEFILER\admin.
User SID – The security identifier. For example, sid=S-1-5-21-2278938113-1352723297-1199027263-1402.
Operation – The operation that was executed. For example, op=open.
Timestamp – The UTC time the operation was executed. For example, timestamp=1609230647.
Local time – The local time the operation was executed. For example, local_time=1609223447.
Root Path – The root path for the share. For example, rootPath=/var/vol/syncgateway/cloudshare|share=cloud.
share – The name of the share. For example, share=cloud.
Path – The path to a file being handled. For example, path=users/portal admin/My Files/Photos/New Microsoft Word Document1.docx.
Destination – The destination for a move or copy operation. For example, destination path=users/portal admin/My Files/Photos/E0EAEC4D.tmp.
Type – Whether the operation is on a folder or file.
Attributes – The attributes, either in readable format, for example, att=org.netatalk.Metadata, or machine readable, for example, dosattrib=0000dosattrib=0000.
Access code – The access code. For example, access=00000100000000000000000000000000.
Remote hostname – The IP address of the device connected using SMB to the edge filer. For example, remote hostname=10.212.134.70.
File size – The size of the file being operated on. For example, Size=18446744073709551615.
Data Read/Write – For example, dataRW=18446744073709551615.
Directory – Whether the operation is on a directory or not. For example, isDir=1.
The operations have the following meanings:
| Operation in Log | Description | Flag in User Interface |
|---|---|---|
| read, OpenDenied | Open a file for reading | List Folder Read Data |
| create, write, createDenied, OpenDenied, move | Create or write to a file Create Files | Write Data |
| create, createDenied, OpenDenied | Create a folder | Create Folders Append Data |
| getea | Get the extended attributes | Read Extended Attributes |
| setea | Set the extended attributes | Write Extended Attributes |
| delea | Delete an extended attribute | Write Extended Attributes |
| open | Open a file | Traverse Folder |
| delete, move | Delete a file or folder | Delete |
| getattrib | Get the attributes | — |
| setattrib | Set the attributes | Write Attributes |
| ACEChanged | Change permissions | Change Permissions |
| ACLAdded, ACLDeleted, ACLProtectionAdded, ACLProtectionDeleted | Change access permissions | Change Permissions |
| setdacl | Set permissions | Change Permissions |
| getsd | The security descriptor of a file or directory is fetched | — |
| setsd, AclDenied | The security descriptor of a file or directory is set | Change Permissions |
| chown, AclDenied | Change the owner | Change Owner |
| deleteDenied | Don’t allow deleting a file or folder | Delete Subfolders and Files |



