CTERA enables centralized data access from any edge location or device without compromising performance or security. In a distributed enterprise with an increasingly remote workforce, the need to ensure unstructured file data is private and secure is paramount for success. Files can contain sensitive enterprise data, such as intellectual property or customer information, and they must be protected from theft, leakage, and loss. Enter Data security posture management (DSPM), a data-first approach to securing data, which enables you to gain a clear view of the where, who and how of your sensitive data: Where it is, who has access to it, and how it has been used.
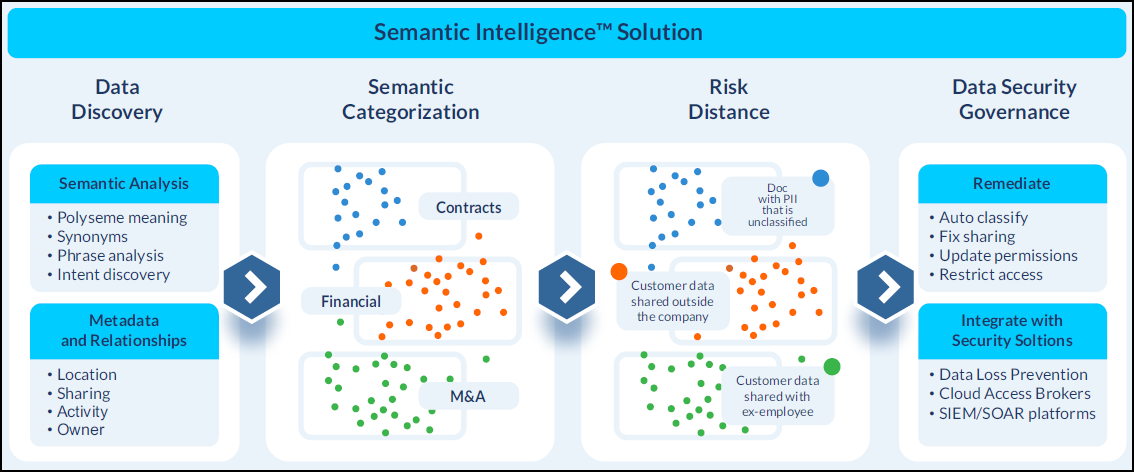
Concentric Semantic Intelligence is a SaaS-based, data security posture management (DSPM) and access governance solution that utilizes deep learning to automatically discover and classify sensitive data, identify risk, and remediate issues.
The CTERA and Concentric solution simplifies data discovery and categorization for organizations by autonomously discovering and categorizing various types of data in CTERA's global file system, such as financial data, PII/PHI/PCI, intellectual property, and confidential business information. Semantic intelligence then allows for remediation of discovered risks.
This is achieved by installing a single, dedicated edge filer as an SMB target near the Concentric proxy server. The Edge Filer allows for efficient, low-latency exposure of metadata and data to Concentric AI proxy, which can then scan the entire global organization's data and apply policies and labels to existing documents. The solution offers enhanced security and compliance capabilities and presents a comprehensive and efficient approach to data discovery and categorization.
For more information about using CTERA with Concentric Semantic Intelligence, contact CTERA. For more information about Concentric Semantic Intelligence, see https://concentric.ai/.
Configuring CTERA to work with Concentric Semantic Intelligence
To utilize Concentric Semantic Intelligence with CTERA, a dedicated CTERA V Series edge filer is deployed near the Concentric Proxy server, to allow the Proxy server to scan the file system using the SMB protocol with a privileged administrator account.
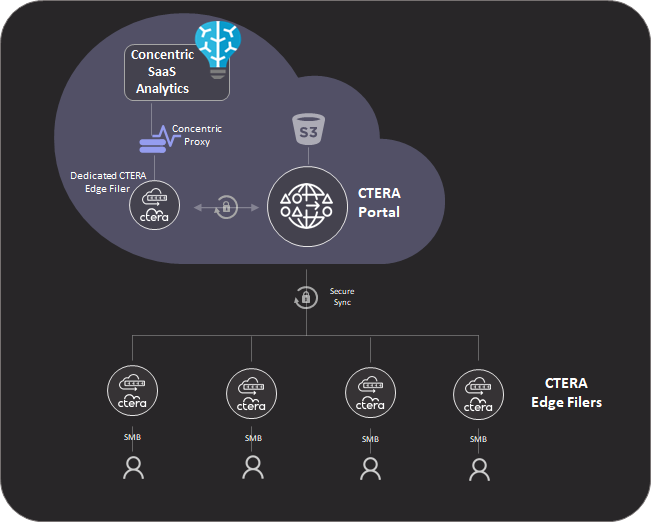
The dedicated edge file should have sufficient RAM and storage space to hold the entire global file system metadata. Sizing the dedicated CTERA Edge Filer, based on the size of the global file system, should be done in coordination with CTERA Support.
To install the Concentric proxy server and set it up, contact Concentric.
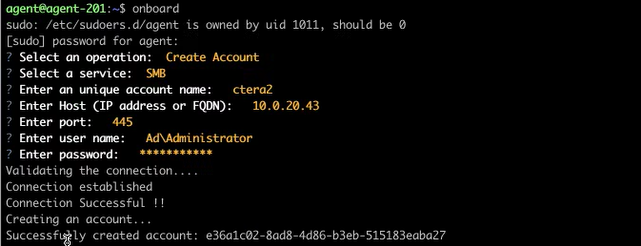
To connect Concentric Semantic Intelligence to the dedicated CTERA Edge Filer:
- Set up the Concentric proxy server to connect to the dedicated CTERA Edge Filer.
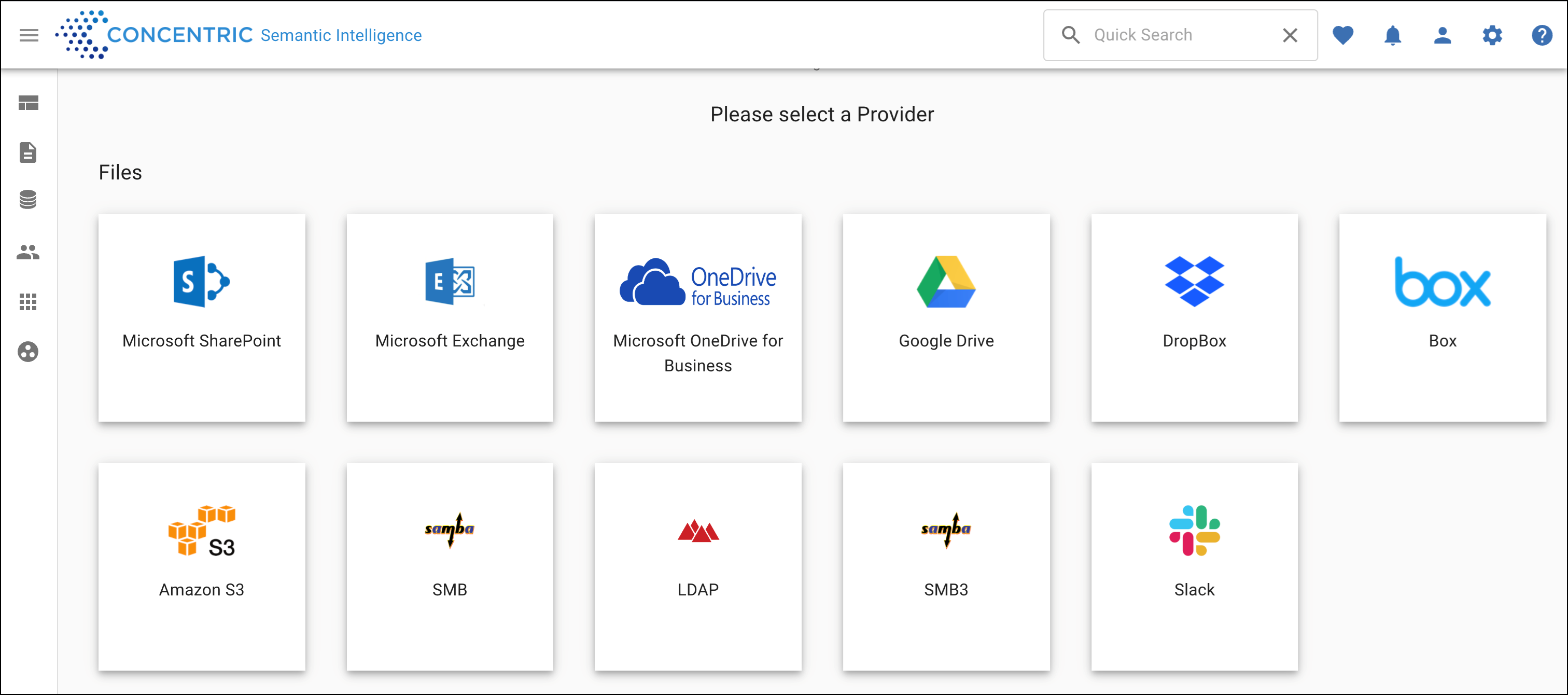
- In Concentric Semantic Intelligence, choose the SMB or SMB3 connector.
- Select Concentric Proxy connectivity.

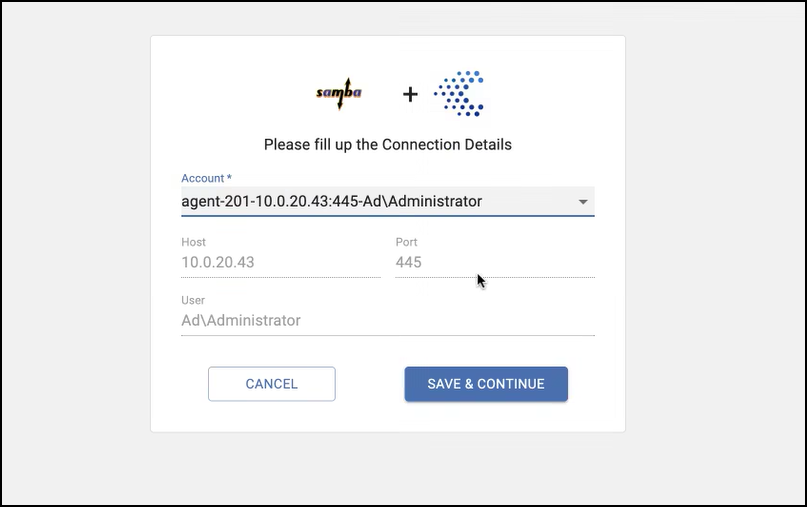
The Concentric Semantic Intelligence connection window is displayed.
 Note
NoteThe provided user name should be an administrator with full read/write permissions in order to allow scanning the entire global file system and performing remediation steps.
- Enter the connection details and click SAVE & CONTINUE.
- Select the folders to scan: either All Files or Let me select.
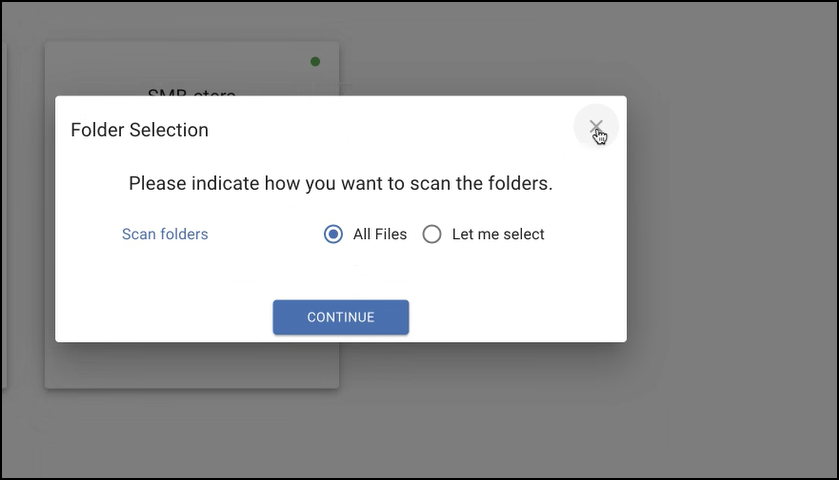
The Concentric Semantic Intelligence dashboard is displayed.
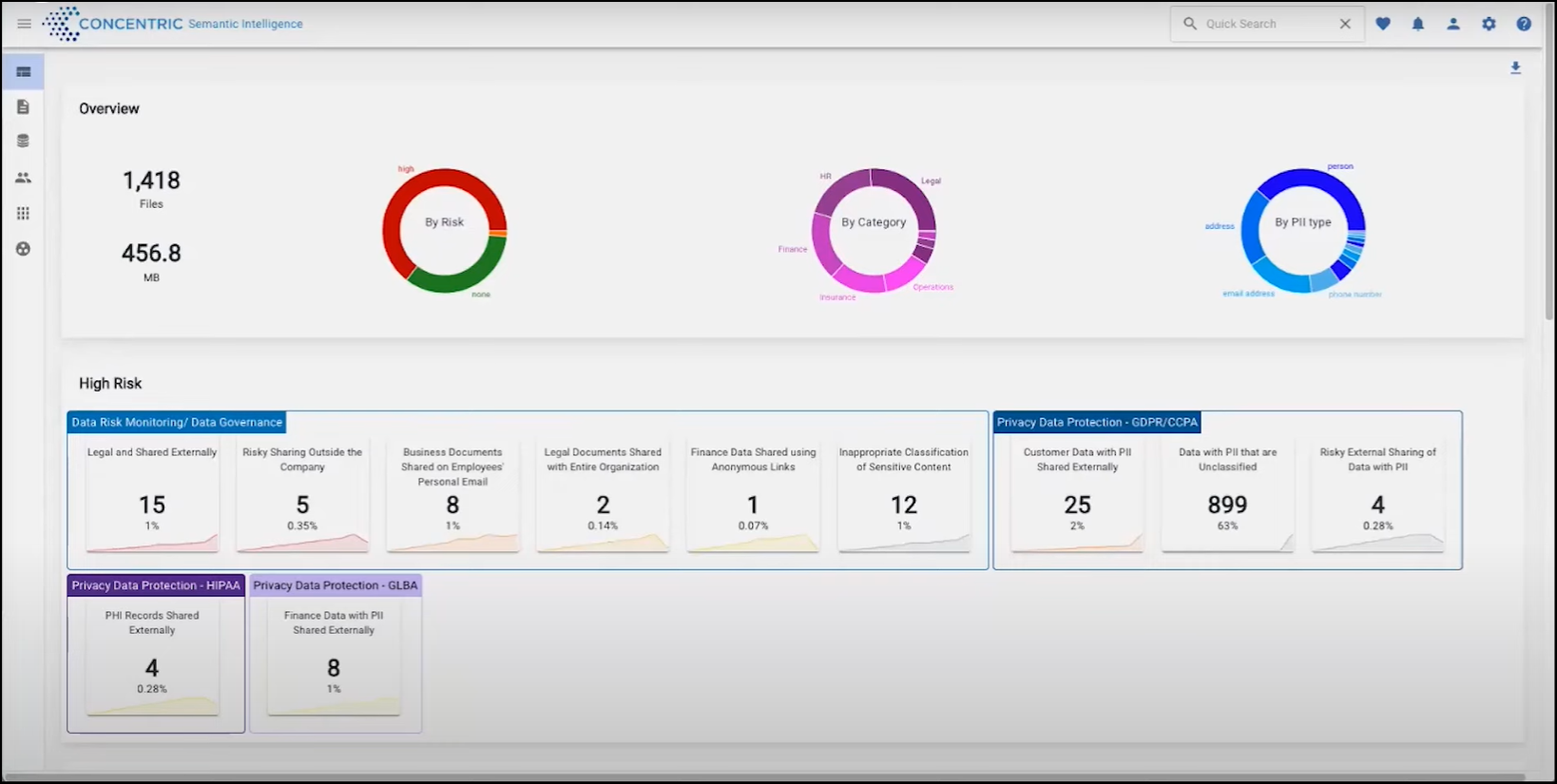
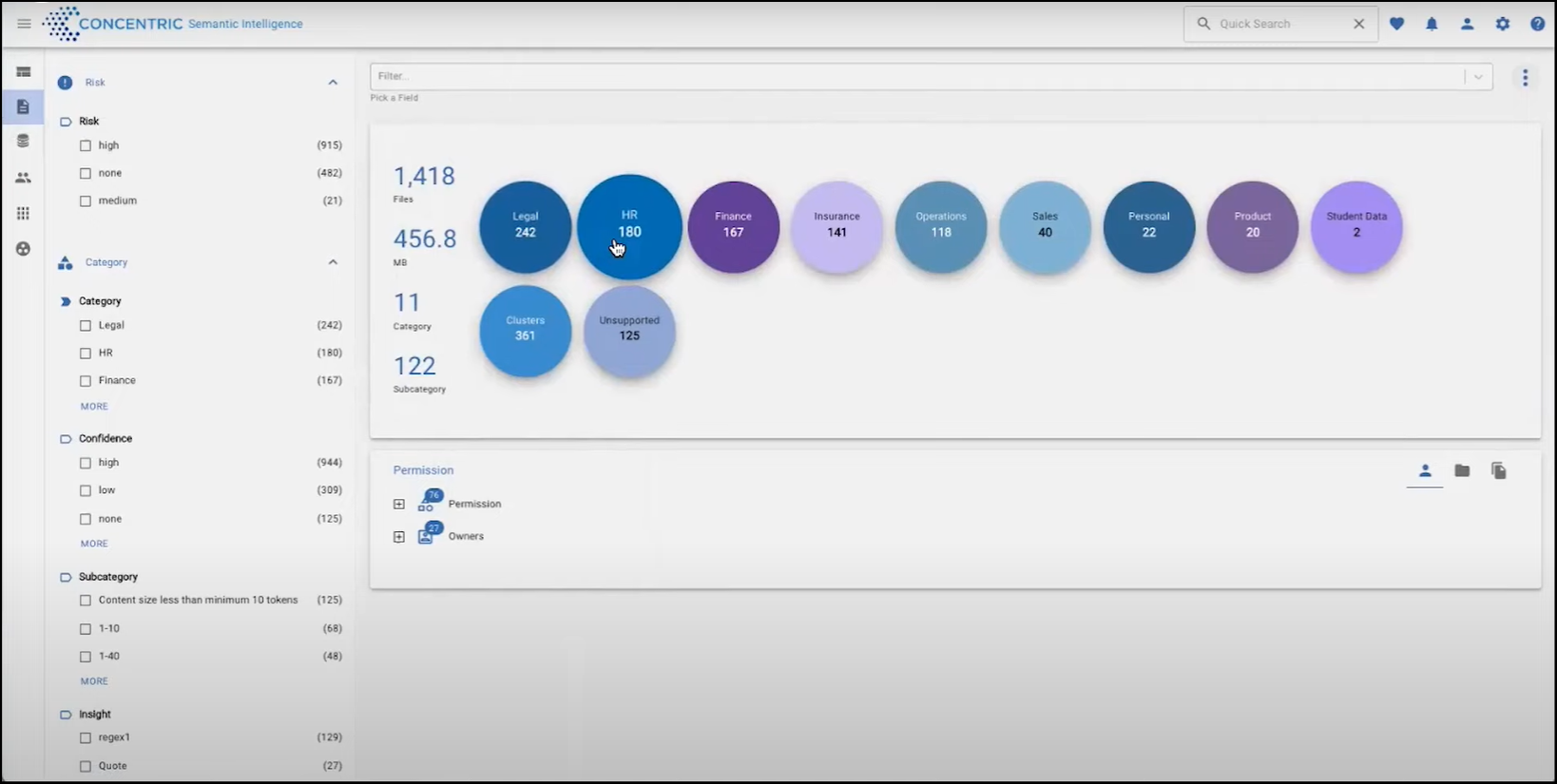
- Concentric Semantic Intelligence analyses the selected files and folders and categorizes the results.
For more information about Concentric Semantic Intelligence, see https://concentric.ai/.